eFuse Settings
eFuse is a one-time programmable (OTP) memory with random access interfaces on SoCs. The eFuse stores product configurations, security mode control information, and keys for encryption and signing.
When using GProgrammer, users can generate eFuse files by specifying product names, IDs, and firmware keys, and by configuring security mode and SWD interfaces.
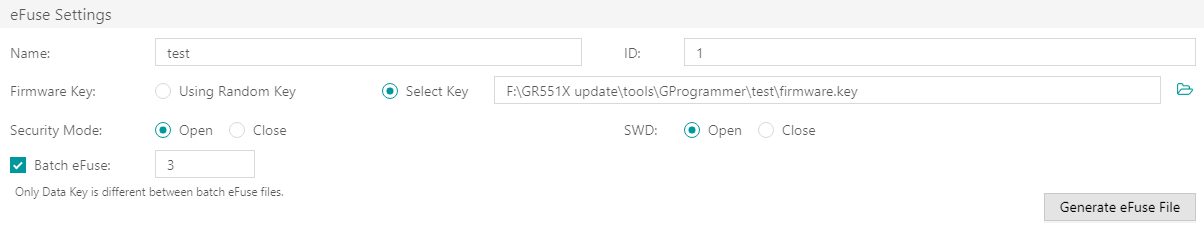
- Firmware keys can be random keys generated by GProgrammer. Users can also add key files on demand.
- When Security Mode is enabled, users can choose to Open or Close the SWD interface.
GProgrammer allows users to generate multiple Encrypt_key_info.bin files in batches by checking Batch eFuse. The generated files are unique, meeting requirements of scenarios demanding one key for one device. For example, when users input “3” in the Batch eFuse box, GProgrammer generates three Encrypt_key_info.bin files: Encrypt_key_info.bin, 2_Encrypt_key_info.bin, and 3_Encrypt_key_info.bin.
Generated files are listed in the figure below:

- efuse.json: a temporary file
- Encrypt_key_info.bin, 2_Encrypt_key_info.bin, and 3_Encrypt_key_info.bin: files to be downloaded to eFuse, covering information on products, encryption, and signing. These files shall be downloaded to and stored in eFuse.
- firmware.key: a private key for encrypting firmware
- Mode_control.bin: an eFuse file covering information on security mode and SWD. This file shall be downloaded to and stored in eFuse.
- product.json: a product information file. This file shall be imported to a GProgrammer when encrypting or signing firmware.
- sign.key: a private key to generate signatures
- sign_pub.key: a public key to verify signatures
- Public_key_hash.txt: a public key hash file to verify signatures
To make files download to eFuse or firmware encryption and signing user-friendly, GProgrammer automatically loads the paths of the Encrypt_key_info.bin file and the Mode_control.bin file to the Download area, and the path of the product.json file to the Product Info pane in the Encrypt and Sign area, as shown in the figure below.

No modification of eFuse-generated files is allowed because any modification may lead to firmware encryption and signing failures.

